Cyber Security Resume Examples + Template for 2025
Create Your Resume NowYou keep information and people safe by finding vulnerabilities and stopping hackers dead in their tracks. Now, you need to write a cyber security resume that sneaks in innocently like a trojan and shocks recruiters with its contents.
No worries. You’re about to get the intel on crafting a cyber security analyst resume that can’t be compromised.
This cyber security resume guide will show you:
- Cyber security resume examples better than 9 out of 10 other resumes.
- How to write a cyber security resume that gets more interviews.
- Tips on how to put skills and achievements on an IT security resume.
- How to describe your experience to get any cyber security jobs you want.
Want to save time and have your resume ready in 5 minutes? Try our resume builder. It’s fast and easy to use. Plus, you’ll get ready-made content to add with one click. See 20+ resume templates and create your resume here.
Sample resume made with our builder—See more resume examples here.
Also, here are some other IT-related resume guides you can follow up with:
- Computer Science Resume
- Data Analyst Resume
- Data Scientist Resume
- Quality Assurance Resume
- IT Resume
- Information Security Analyst Resume
- System Administrator Resume
- Network Administrator Resume
- Data Center Technician Resume
- Network Engineer Resume
- Example Resumes for All Kinds of Jobs
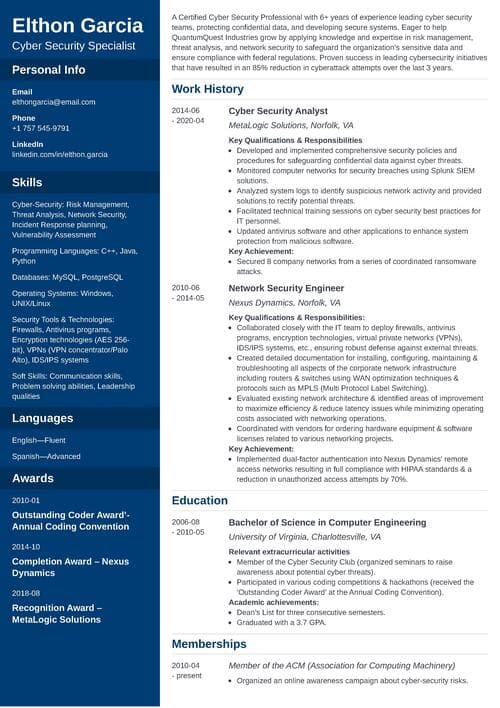
Cyber Security Resume Example
Ethan Carter
Cyber Security Analyst
(555) 234-5678
ethan.carter@email.com
linkedin.com/in/ethan-carter | www.ethancarter.com
Summary
Cyber Security Analyst with 6+ years of experience identifying vulnerabilities, mitigating security risks, and implementing threat detection strategies. Skilled in network security, penetration testing, and compliance frameworks. At ShieldTech Solutions, led a security audit that reduced system vulnerabilities by 35%. Eager to leverage cyber defense expertise to strengthen security posture at Sentinel Cyber Defense.
Experience
Cyber Security Analyst
ShieldTech Solutions, San Francisco, CA
April 2018–February 2025
Key Qualifications & Responsibilities
- Monitored network traffic and conducted real-time threat analysis to detect and mitigate cyberattacks.
- Performed vulnerability assessments and penetration testing to identify security weaknesses.
- Developed and implemented security policies, ensuring compliance with NIST, ISO 27001, and SOC 2 regulations.
- Investigated security breaches and conducted forensic analysis to determine attack vectors and impact.
- Provided security awareness training for employees, reducing phishing-related incidents by 40%.
Key Achievement
- Led a company-wide security audit that reduced system vulnerabilities by 35% and strengthened compliance posture.
IT Security Analyst
CyberSafe Enterprises, Austin, TX
June 2016–March 2018
Key Qualifications & Responsibilities
- Managed firewall configurations, intrusion detection systems (IDS), and endpoint security solutions.
- Assisted in developing incident response plans, ensuring rapid threat mitigation.
- Conducted risk assessments for new software and IT infrastructure implementations.
- Collaborated with developers and IT teams to implement secure coding practices.
Key Achievement
- Designed an automated security monitoring system that improved incident detection time by 25%.
Education
Bachelor of Science in Cyber Security
University of Texas, Austin, TX
September 2012–May 2016
Skills
- Threat Detection & Incident Response
- Network Security & Firewall Management
- Penetration Testing & Vulnerability Assessments
- Security Information & Event Management (SIEM)
- Cloud Security (AWS, Azure)
- Risk Management & Compliance (NIST, ISO 27001, SOC 2)
- Security Awareness Training
- Digital Forensics & Malware Analysis
Certifications
- Certified Information Systems Security Professional (CISSP), 2020
- Certified Ethical Hacker (CEH), 2019
- CompTIA Security+, 2018
Awards
- Cyber Defense Excellence Award – ShieldTech Solutions, 2023
- Security Innovation Award – CyberSafe Enterprises, 2017
Memberships
- Member, Information Systems Security Association (ISSA)
- Member, EC-Council Certified Ethical Hackers (CEH) Community
- Member, ISACA Cybersecurity Professionals
Interests
- Ethical Hacking & Penetration Testing
- AI in Cybersecurity Threat Detection
- Open-Source Security Research
- Cybersecurity Awareness & Training Initiatives
1. What’s the Best Format for a Cyber Security Resume?
Like a standard antivirus checkup, hiring managers first scan each resume and mark those they’ll want to revisit.
In this case, however—
It’s only a quick, 6-second glance the first time ‘round.
And, if you don’t make it past this first skimming, your chances at this company come to an immediate end.
Choose the chronological format.
This format keeps your cyber security resume in order like a great security policy framework. Hiring managers and security agency staff love this format for being familiar and easy to follow.
Here’s how to organize a cyber security analyst resume:
- Start at the top with a compelling IT security resume objective or summary statement.
- List any past experience, including relevant cyber security duties and achievements.
- Write an education section with relevant IT and cyber security coursework.
- Add your cyber cryptography and criminology skills to win them over to your side.
- Include any cyber certifications, security clearances, and other sections to stand out.
Keep your resume legible by choosing the best fonts. Make efficient use of white space and headings to guide their eyes through the various resume sections.
Haven’t worked in cyber security before?
Since your education section is more relevant, place that above your work history section.
Pro Tip: Save your resume for cyber security in the PDF format. The PDF format renders it correctly, no matter which device the hiring manager calls 127.0.0.1.
Not convinced using the reverse-chronological format is right for your information security resumes? There are other options. See our guide: Best Resume Format: What Resume Model to Choose? [+ Resume Format Examples]
2. Cyber Security Resume Objective or Summary?
If you don’t intrigue HR from the very beginning, they’ll shut you down like a basic firewall and quarantine your resume.
How to captivate them?
Write a super-compelling resume summary or resume objective.
Worked in cyber crimes or defense before?
Use a resume summary.
This short paragraph gives your best skills and most relevant experience. A key win with numbers is thrown in as a bonus.
Here’re two cyber security resume examples of summaries:
Cyber Security Resume Examples: Resume Summary
| right |
|---|
| Persistent, detail-oriented cyber security analyst with 3+ years experience with government security software contractor. DoD security clearance. Identified the 2018 Kluxnet virus, saving over 30,000 computers from destruction. |
| wrong |
|---|
| Working as an information security analyst for the last three years, I’ve become quite good at filtering out bad actors. I implemented firewalls, managed access control, quarantined infected machines, and reported security breaches. |
In the wrong example, you give some duties, but they have no idea how well you fulfilled them. The right example, however, gives a winning accomplishment with numbers to back it up—
One’s weak like a 4-digit PIN, while the other is as strong as quantum encryption.
Now—
The only virus you’ve come into contact with professionally was when seeing a doctor for the flu?
No problem!
Use a resume objective when you don’t have paid cyber security experience.
The objective statement on a entry-level cyber security resume tells the agency your career goals. Like the summary, use relevant experience, skills, and achievements to beef it up.
Here are two cyber security analyst resume sample objectives:
Entry-Level Cyber Security Resume With No Experience Samples: Resume Objective
| right |
|---|
| University IT graduate with cyber security background and hundreds of classroom hours in cloud safety, automation, and digital forensics. Seeking to leverage newly-minted top secret security clearance and 4.0 GPA to become the next network security engineer at Astoria Tech. |
| wrong |
|---|
| Having just graduated from university, I don’t have much experience with cyber security. However, I am a fast learner, so I think I’d make a great addition nonetheless. |
The wrong example is like the Nigerian Prince scam—
No one but your great grandfather will find it compelling.
The right one tells them that, though you’re only fresh out of uni, you’ve got what it takes to combat the most significant threats on their behalf. And, using their name is an excellent way to grab their attention.
You’ll obtain interview authorization in no time!
Pro Tip: On any cybersecurity resume, the resume objective or summary goes at the top. However, it doesn’t mean you have to write it first! Save it for the end so you have the rest of your resume to help inform the writing of your heading statement.
Want more advice on writing a career summary or career objective on a resume for cyber security jobs? Check out our guides: Professional Resume Summary Examples [20+ Resume Summary Statement Examples] and General Resume Objective Examples [20+Examples of Great Career Objectives]
Making a resume with our builder is incredibly simple. Follow our step-by-step guide, use ready-made content tailored to your job and have a resume ready in minutes.
When you’re done, our online resume builder will score your resume and our resume checker will tell you exactly how to make it better.
3. How to Describe Your Cyber Security Experience
Information security analysts and cyber security jobs in the US will grow by an eye-popping 28% between 2016–2026.
That’s more than 28,000 new people for you to compete against—
A lot of competition.
How to beat the other candidates?
Write a work experience section that isolates your resume as important (like a governmental computer system air gap).
Here are two information security resume samples:
Cyber Security Resume Examples—Job Description
| right |
|---|
Cyber Security Analyst Key Qualifications & Responsibilities
Key Achievement
|
| wrong |
|---|
Information Security Analyst Key Responsibilities
|
Like a computer without antivirus software, the wrong one is missing something crucial—
Perfectly-chosen cyber security duties and quantifiable accomplishments which the right one included.
But, what if you haven’t been on a paid Cyber Defense League?
Not to worry.
Here’s how you list other experience in a way that’s relevant to cyber security jobs:
Entry-Level Cyber Security Resume No Experience
| right |
|---|
Website Consultant Key Qualifications & Responsibilities
Key Achievement
|
Here, for example, you consulted on multiple aspects of a client’s website, from design to content placement. However, you only listed relevant responsibilities and achievements for an infosec job.
That’s how it’s done!
Pro Tip: Got an internship, such as the Cybersecurity Internship Program from the U.S. Department of Homeland Security? Add them to your work history section, as well.
Got no experience whatsoever? Don’t worry! See this guide: First Resume with No Work Experience Examples
4. Is Your Education Section Underperforming? It Might Be
Hiring managers are like identity management systems—if you don’t have the right permissions, passage not given.
How to be granted access to the cyber security interview?
Whether it’s an IT security manager resume or a junior-level cyber cryptography resume, your education section has to deliver.
Here’s how to list education on your infosec resume:
Cyber Security Analyst Resume Examples—Education Section
BS in Cyber Forensics and Information Security
Cornell University. Ithaca, NY
Relevant Coursework: Network Forensics, Cyber Crime, Database Security, Ethical Hacking, Penetration Testing, Vulnerability Analysis, National Security, Malware Analysis, Network Intrusion Detection.
What if you’re still working on your degree?
Add an unfinished degree like this:
Majoring in Cybersecurity (Cyber Operations Concentration)
Excelsior College, Albany, NY
Expected Graduation: 2021
Relevant Coursework: Cyberattacks and Defenses, Computer Forensics, Cryptography, Risk Management, Web Architecture, Access Control and Intrusion Detection Technology, Security Defense Countermeasures.
Only have high school?
Most cyber security jobs require at least an associate degree and/or a valid cyber security certificate. Check the job ad for the educational requirements.
If applying for a lower level job, such as for a cyber security intern or junior cyber security analyst, add high school like this:
Townsend Harris High School, Flushing, NY
Graduated: 2014
Don’t add high school if you have a completed college degree. Otherwise, add it as a second entry.
Finally, if your education is more relevant than your work history, put the education section on top.
Pro Tip: To get a great job in cyber security, employers love to see breadth over depth. Show them you have other IT knowledge, such as scripting languages (Python, Bash, etc.), for example. Also, data analysis is always a great bet.
Took a less-common educational path to get where you are? Check this guide out: Education Resume Section: How to List High School & College Education
5. How to Put Skills on a Cyber Security Resume
You know you’ve got mad hacking skills.
However—
All your competitor cyber security candidates do, too.
Show the recruiter they’re all MD5 while you’re SHA-3.
But which cyber security skills?
First, make a basic list of cyber security skills. Add both hard and soft skills.
Hard skills are those you study and learn (e.g., detecting intrusions and vulnerabilities), and soft skills are ones you work on throughout your life (e.g., being a great communicator).
Cyber Security Skills for a Resume
CS Hard Skills | CS Soft Skills | CSA Domains |
Malware Analysis | App & Interface Security | |
Risk Analysis | Attention to Detail | Audit Assurance & Compliance |
Python Scripting | Problem Solving | Business Continuity Mgmt & Operational Resilience |
Intrusion Detection | Collaboration & Teamwork | Change Control & Configuration |
Data Analytics | Data Security & Information Lifecycle Mgmt | |
Programming | Datacenter Security | |
Cloud Security | Accountability | Encryption & Key Mgmt |
Encryption | Interpersonal Skills | Governance & Risk Mgmt |
Automation/Devops | Works Well Under Pressure | Identity & Access Mgmt |
Security Analysis | Infrastructure & Virtualization | |
Risk Mitigation | Interoperability & Portability | |
Reverse Engineering | Mobile Security | |
Secure Software Development | Analytical and Diagnostic Skills | Security Incident Mgmt, E-Discovery & Cloud Forensics |
Incident Response | Supply Chain Mgmt, Transparency & Accountability | |
SIEM Tools | Threat & Vulnerability Mgmt |
But, just adding all those skills to your resume willy-nilly is like sending credit card information over an unencrypted channel—
Not a brilliant idea.
Instead, use the job ad to help you decide which skills are most important to them.
Here’s an example cyber security job description:
- Perform and manage technical evaluation and penetration testing of internally- and commercially-developed applications (web, desktop, and mobile), systems, and medical devices. [1]
- Assist in evaluating and developing the security controls for IT solutions of all types (mobile, web, client-server, etc). [2]
- Maintain current knowledge of security vulnerabilities, threats, and industry standard methodologies (both within and external to the healthcare industry).
- Participate in appropriate and relevant conferences and courses to maintain technical proficiency.
- Assist in developing and implementing an annual personal education plan to develop and maintain currency of security-related skills, technologies, methodologies, and standard methodologies. [3]
Based on the job description, there’s a right way and a wrong way to list your IT skills:
Cyber Security Analyst—Skills Section
| right |
|---|
|
| wrong |
|---|
|
The wrong skills here is like using your birthday as a password—
Weak sauce.
The right example of resume skills section copies their needs like a keylogger—in a good way. It’s tailored to be exactly what they’re looking for.
Last but not least, don’t forget about the ATS.
Larger companies receive dozens (or more) applications every day. An applicant tracking system is software which helps them manage these.
An HR manager scans resumes into the ATS, and then they give the program specific resume keywords to look for.
The best-matching ones get whitelisted for the job.
We’ve analyzed over 11 million resumes created using our builder, and we’ve discovered that:
- Cyber Security Analysts usually list 20 skills on their resumes.
- The most common skills for Cyber Security Analysts and Cyber Security Specialists include network security management, vulnerability assessment, ICT disaster recovery, incident response, and digital forensics investigation.
- Resumes for Cyber Security Analysts are, on average, 2.7 pages long.
6. How to Add Other Sections for an Effective Cyber Security Resume
You could hack the hiring manager to show them you’ve got what it takes for this cyber security job.
But that might not go over so well.
Instead, set yourself apart from the rest of the candidate crowd by adding extra resume sections.
Here are the best suggestions for an IT security resume:
Cyber Security Resume Example: Extra Sections
1. Security Clearances
The most demanding cyber security positions, such as government contractor positions, require a security clearance. If you already have one from your time in the military, for instance, you’re one long step ahead of the others!
Here’s a security clearance on resume sample:
- Top Secret w/ Sensitive Compartmented Information Clearance 2018 DoD
- Full Scope Polygraph - 2019
- Counterintelligence (CI) Scope Polygraph (CSP) - 2017
For most cyber security pros, certifications are often weighed more heavily than 4-year degrees.
Here are some great internet security certificates to add to your resume:
- Certified Ethical Hacker (CEH)
- Certified Information Security Manager (CISM)
- CompTIA Security+
- CompTIA Cybersecurity Analyst (CySA+)
- CompTIA Advanced Security Practitioner (CASP+)
- CompTIA Penetration Tester (PenTest+)
- Certified Information Systems Security Professional (CISSP)
- SANS GIAC Security Essentials (GSEC)
- Offensive Security Certified Professional (OSCP)
Volunteered helping the local adult care facility get past their ransomware attack? Not only are you awesome, but it adds great experience to your cybersecurity resume.
Just skip anything irrelevant to cryptovirology and internet security.
Did you work for yourself doing some online gigs? Add those in a separate section, as well!
4. Languages
IT companies are global companies. To set yourself apart, add knowledge of a second language to your resume.
We’ve got great guides on the best things to add to a resume and which resume sections and categories to include. Check them out!
Pro Tip: In the US, according to the NSA, you’re permitted to post your security clearance on a resume. However, it gets quite strict after that. Projects must be anonymized, place names withheld—read the full guidelines before you submit your resume.
7. How About a Cyber Security Cover Letter?
A resume without a cover letter is like an asymmetric public key without the corresponding private key—
Useless.
You must attach a cover letter, as more than half of employers say a resume alone is not enough. It’s a powerful one-two punch by using multiple attack vectors.
Here’s how to write cyber security cover letters they’ll eat up:
- Start your IT security officer cover letter with a compelling opening statement.
- Tell them why you’re the perfect candidate to solve their future cyber concerns.
- Explain why this particular company and position are ideal for you.
- Close it with a call-to-action as simple-but-powerful as a brute-force attack.
Pro Tip: Use Grammarly and proofread your cyber security resume before you send it off. How will they have any confidence in your tech skills if you can’t even use spell check?
Want more cover letter tricks that always work? See these articles: 35+ Best Cover Letter Tips, Advice & Guidelines and How to Write a Job-Winning Cover Letter in 8 Simple Steps (12+ Examples)
Plus, a great cover letter that matches your resume will give you an advantage over other candidates. You can write it in our cover letter builder here. Here's what it may look like:
See more cover letter templates and start writing.
Key Takeaway
So, now you have a cyber security resume that’s malware-free and runs like a dream.
Let’s sum it all up.
Here’s how to write a cyber security resume:
- Use the reverse-chronological resume format to make it easy to read and follow.
- Start with a heading summary or resume objective which makes them continue.
- List your work experience with appropriate duties and winning accomplishments.
- Add an education section which plays up any cyber security coursework you had.
- Include IT and security skills using resume keywords from the job ad.
- Improve your chances with extra sections, like clearances and certifications.
- Attach a cyber security cover letter before you send your resume off.
Now THAT’S a resume that launches a denial of service attack on your competitors!
Got any questions on how to write a cyber security analyst resume? Not sure how to talk about network security skills or IT achievements? Get at us in the comments below, and thanks for reading!
About Zety’s Editorial Process
This article has been reviewed by our editorial team to make sure it follows Zety's editorial guidelines. We’re committed to sharing our expertise and giving you trustworthy career advice tailored to your needs. High-quality content is what brings over 40 million readers to our site every year. But we don't stop there. Our team conducts original research to understand the job market better, and we pride ourselves on being quoted by top universities and prime media outlets from around the world.
Sources
- https://www.bls.gov/ooh/computer-and-information-technology/information-security-analysts.htm
- https://www.dhs.gov/homeland-security-careers/cybersecurity-internship-program-0
- https://www.eccouncil.org/programs/certified-ethical-hacker-ceh/
- https://certification.comptia.org/certifications/security
- https://certification.comptia.org/certifications/cybersecurity-analyst
- https://certification.comptia.org/certifications/comptia-advanced-security-practitioner
- https://certification.comptia.org/certifications/pentest
- https://www.nsa.gov/Portals/70/documents/resources/everyone/prepub/resume-dos-donts.pdf